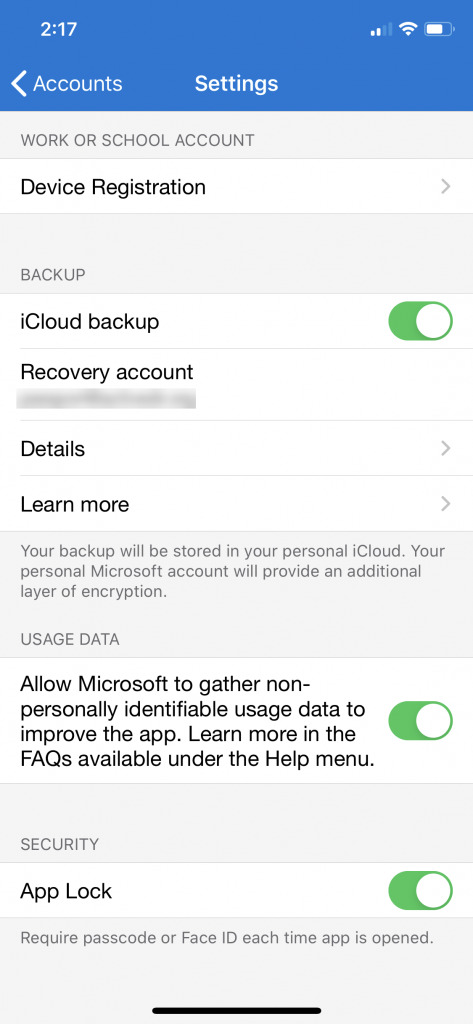
If you are using Microsoft Authenticator for MFA or for signing in to your accounts then you should give some thought to enabling the App Lock feature. App Lock requires you to authenticate (using biometric or PIN) before opening the app for use. This is a very handy feature given the potentially sensitive information the app contains (Global Admin anyone?).
If you’re already protecting your device with a PIN or biometrics you could argue that you don’t need the extra hassle of another authentication gate, but it seems good practice to turn it on. Here’s how to do it. Go to the hamburger menu (three horizontal lines) on the top left of the Authenticator main screen. Choose the Settings option. From there, enable the App Lock option under the Security menu by turning the slider so it shows green.
Now when you need to open the app to sign or complete an MFA challenge, you will first need to authenticate with your PIN or a biometric method.
It would be really useful if there was a way in which the App Lock feature could be enabled and enforced centrally as part of a corporate policy. Unfortunately, this capability doesn’t exist right now. Microsoft has shied away from making this type of control available via Intune MAM policy for the simple reason that MAM often uses Authenticator as its mechanism of enforcement.
One final thing to highlight is the impact of App Lock for those using Authenticator with Apple Watch. You may need to set up your Apple Watch approvals again after enabling the App Lock, but you will still be able to complete approvals on the watch. Anecdotally, it seems as though people have slightly different experiences with Apple Watch, so don’t be surprised if yours doesn’t work as seamlessly as you would hope.
Update 4 August 2020. App Lock is now enabled by default.


Hey,
I don’t really understand this sentence “Microsoft has shied away from making this type of control available via Intune MAM policy for the simple reason that MAM often uses Authenticator as its mechanism of enforcement.”.
I did not find sources of MS talking about this, I looked in Intune and didn’t find anything configurable.
The second part of sentence is not very clear especially, in what way is authenticator app used for enforcing MAM? I would expect in cae of MAM the specific app is always responsible to enforce the restrictions (since device is not enrolled so no Intune agent).
I believe the source is here:
https://twitter.com/A_Mieth/status/1096502350330642443